Encryption and decryption
When a message is passed from one computer to another, it is easy for it to be hacked, with a third party decrypting or tampering with its contents.
So, to encrypt a message, there must be an algorithm for encryption and decryption. However, since this algorithm alone cannot solve the problem, there must be a means to prevent the encrypted message from being decrypted even if an obvious algorithm is in front of us, that is, a key. Key-based encryption is commonly used as an encryption algorithm, and the length of the encryption key varies from 1 bit to several hundred bits.
Even if a hacker manages to obtain the encrypted message and even the algorithm, he must have the key to decrypt it. If the key is 128 bits long, then one of 2^128 encryption keys would be correct, which would take 10,790,283,070,806,014,188 years, even with a multi-billion supercomputer that takes 1/1,000,000,000,000 seconds to crack.
Asymmetric and symmetric keys
Cryptographic keys are broadly categorized into asymmetric and symmetric keys. An asymmetric key is a pair of keys, meaning that encryption with one key cannot be decrypted without the other. A symmetric key requires that the key used to encrypt and the key used to decrypt are the same. Taking advantage of this property, computer networks often mix symmetric and asymmetric keys to transmit encrypted messages.
For example,
Host A wants to securely deliver an encrypted message to Host B. A creates a pair of asymmetric keys, keeps one for himself and sends the other to B. The key that A owns is called the Private Key, and the key sent to B is called the Public Key.
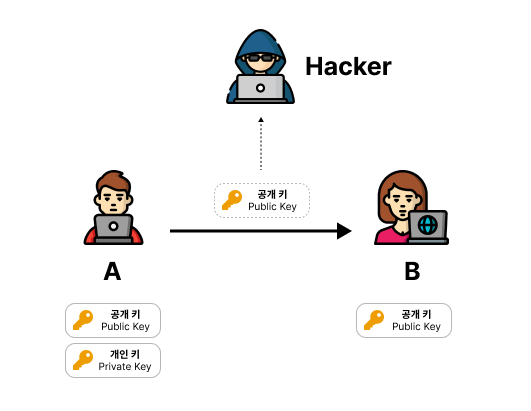
B encrypts the public key received from A with its symmetric key and sends it to A. A decrypts the received symmetric key with its private key and shares the symmetric key created by B. In this process, even if the hacker obtains the public key and the encrypted symmetric key, he or she does not have the private key and cannot know the contents of the symmetric key.
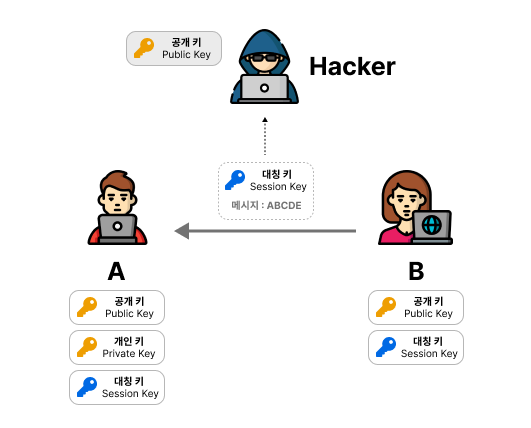
Now, A encrypts the contents of the message with the symmetric key it received from B and sends it back to B. B can decrypt the encrypted message with the symmetric key to verify its contents. Again, the hacker cannot decrypt the message because he does not have the symmetric key.
If a hacker tampered with the message and sent it to B, B would not be able to decrypt it.
Last updated